How to Choose the Best Remote Access Option
If you could pick one thing that changed dramatically for businesses due to the pandemic, what would it be? I think most of us would say the need to work remotely.
Since 2020, remote work has become vastly more commonplace, and now is a great time to make sure your remote workforce is accessing resources safely.
Over the last decade or so, two technologies have become commonplace in our discussions of remote access, though I suspect many don’t know anything about them beyond their acronyms: RDP and VPN.
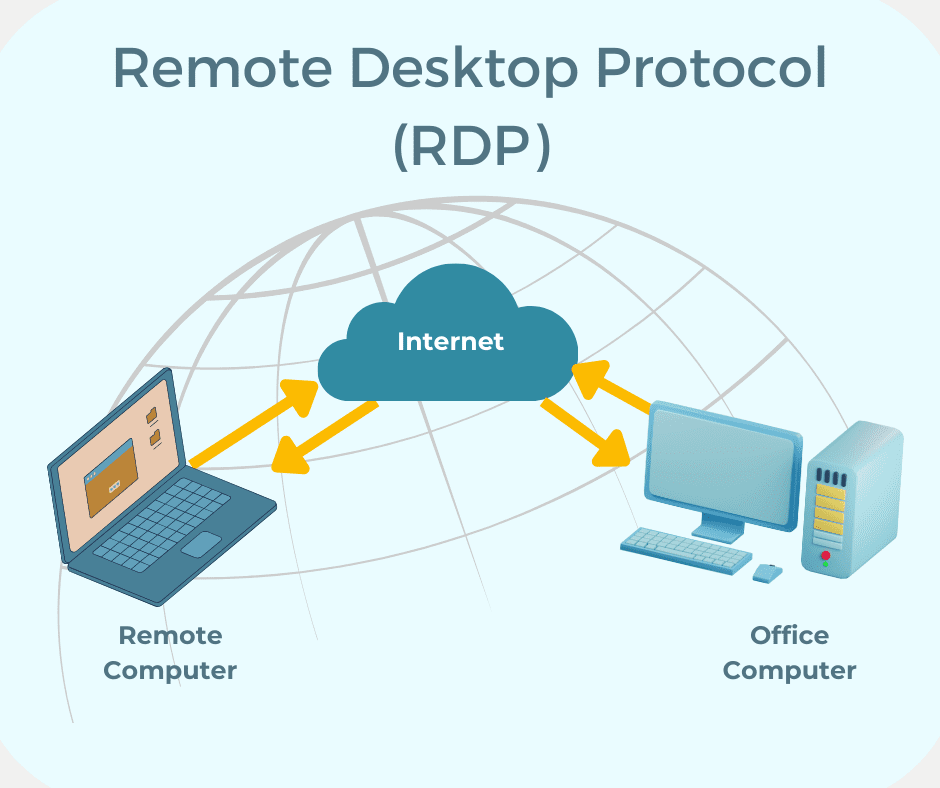
RDP: Remote Desktop Protocol
RDP provides an easy way to access a remote computer as if you were sitting down in front of it. It is, essentially, screen sharing.
This makes for a great user experience because it allows the user complete access to all network resources, including printers, that are in the office setting. Anything you can do in your office you can do with RDP.
Even better, RDP is essentially free in many cases. I say essentially because it does have a few requirements. The key requirement is a computer on the other end that you can connect to!
Simple, right? Well, not so fast.
What about your users who have only a laptop, which is connected to a docking station in the office, which they take home every day? What are they going to connect to in the office?
That brings me to the not-so-free component of RDP: the Terminal Server.
Think of a terminal server like a bunch of computers, just sitting there waiting to be remotely accessed. Of course, this requires a dedicated computer (most likely a server), and every connection will require a paid license. That can get expensive quickly, but it’s still a great solution for the remote workforce.
Is RDP safe, though?
The answer is: it depends. But by itself, no, it’s really not.
As with any older technology (RDP has been around since 1998), enterprising hackers have found ways to exploit it. Without getting too far into the weeds, just know that RDP uses well-known communication protocols and, because they are so well-known, hackers will be looking for them when trying to gain access to a network.
So, if it’s not safe by itself, why do we still use it and how do we do so safely?
Enter VPN: Virtual Private Network
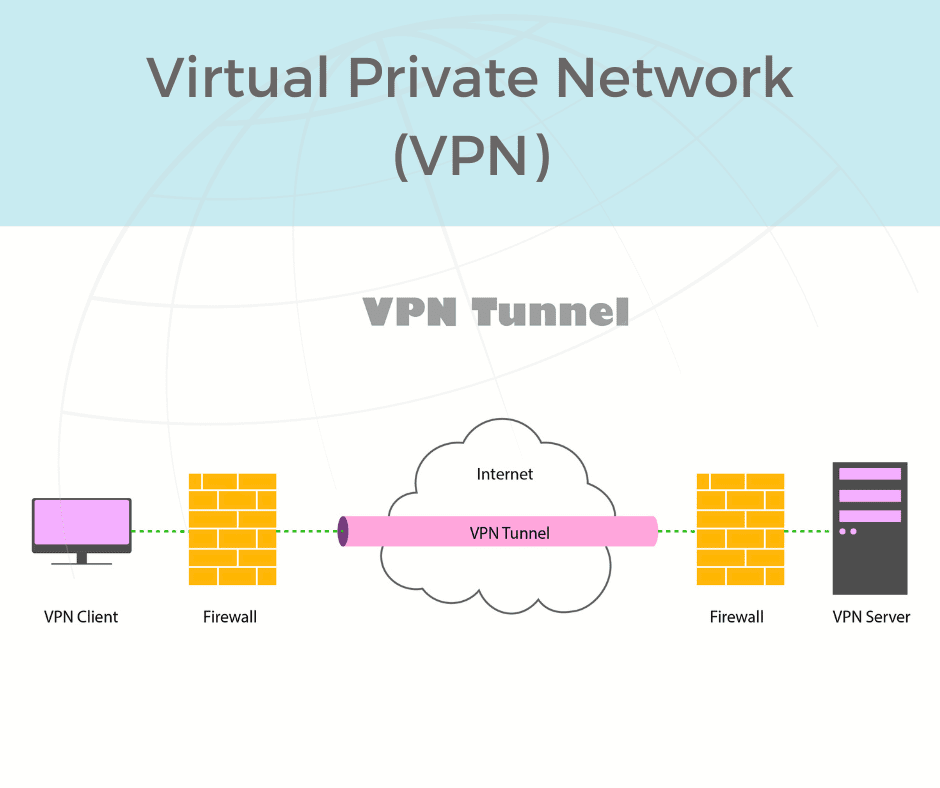
You’ll often hear a VPN described as a tunnel, which is a great way of thinking about it.
When you connect to a VPN, you are carving out a tunnel on the internet that takes you straight to the office network. That tunnel is private, and only you can use it. In that way, it’s secure.
VPNs are incredibly useful tools for remote access, but they don’t come without cost. Most VPNs are going to require a dedicated firewall for the network you are accessing.
Your home network is one end of the tunnel, and the firewall is the other. In some cases, the firewall will require a paid license for every person connected to it, though most firewalls do include at least some licensing for more than one user. The number of VPN connections your corporate firewall supports will be determined by the firewall manufacturer.
If VPNs are safe, why don’t we use them instead of RDP?
The easy answer is, we don’t have to choose one over the other. They can, and often are, used together.
Think of it this way, if the communication that RDP uses isn’t safe by itself, why not have that communication through a secure “tunnel” that only you have access to. The computer, or perhaps the Terminal Server, can sit behind the firewall without announcing to the world that it’s open for connections, and only talk to users through VPN tunnels.
This is a great solution for a couple of reasons. One, that computer isn’t announcing its availability to potential hackers. Two, VPNs can be a bit slow (the cost of making the communication secure), and not all applications will work with just a VPN connection.
The speed issue is easily dealt with through RDP. All the work you do with an RDP connection takes place on that office computer or server, so the only data traveling back and forth from home to office are screen captures. This combination can be a great compromise and in practice works quite well.
- 36% of remote workers used public Wi-Fi networks, which are inherently insecure and can expose sensitive information.
- 40% of respondents had their information compromised while using public Wi-Fi. [Forbes]

Conclusion
While RDP is often free or inexpensive, if you want to make sure your business’ data remains secure, using only RDP isn’t your best choice.
VPNs by themselves can be slower, which employees never enjoy, but offer far greater security for remote work.
Combining the benefits of VPNs and RDPs can be a great option, but do you know which additional devices (firewalls, switches, etc.) your network needs?
We know this can all be quite confusing. Are you still not sure what would be best for your company, and would like some assistance? Contact us today to ask how PCA’s expert technicians can assess your remote work environment to make the best recommendation for your business needs.
Robbie Anderson
Sales Solutions Expert, PCA Technology Solutions
With over 25 years of extensive experience in the dynamic landscape of the IT industry, Robbie Anderson is a seasoned Sales Engineer dedicated to delivering innovative solutions tailored to meet the diverse needs of clients. Robbie has been an integral part of PCA Technology Solutions since 2002, consistently driving excellence and fostering long-term client relationships. Passionate about problem-solving and equipped with deep industry knowledge, Robbie thrives on the challenge of identifying and implementing optimal solutions for clients. Whether it’s crafting bespoke solutions or providing insightful guidance, Robbie remains steadfast in the pursuit of excellence.