Vendor email compromise (VEC) and business email compromise (BEC) are both types of phishing attacks that target businesses.
However, there are some key differences between the two types of attacks.
BEC attacks target businesses directly. The attacker impersonates a senior executive at the target company and sends fraudulent emails to employees, requesting payment for an overdue invoice or asking for sensitive information, such as W-2s, personally identifiable information (PII), or payment information.
Often, this BEC form of attack is difficult to identify because it is sent through spoofed email accounts that resemble the actual email address of the person they are posing as.
The emails can easily go unnoticed by traditional email security solutions because they do not contain malware, malicious links, dangerous email attachments or other elements the email security solution uses to filter and identify phishing emails.
BEC emails use plain text carefully designed and crafted to trick the recipient and to avoid existing security techstack. The emails are typically phrased in a way that mimics the tone and content of trusted senders such as coworkers or CEO, which helps trick the recipient into engaging with them.
VEC attacks target businesses that have a relationship with a third-party vendor.
The attacker gains access to the vendor’s business email account and then uses that account to send fraudulent emails to the vendor’s customers.
The emails often appear to be from a legitimate source, such as the vendor’s CEO or CFO, and they may request payment for an overdue invoice or ask for sensitive information, such as credit card numbers or passwords.
Key differences between VEC and BEC attacks:
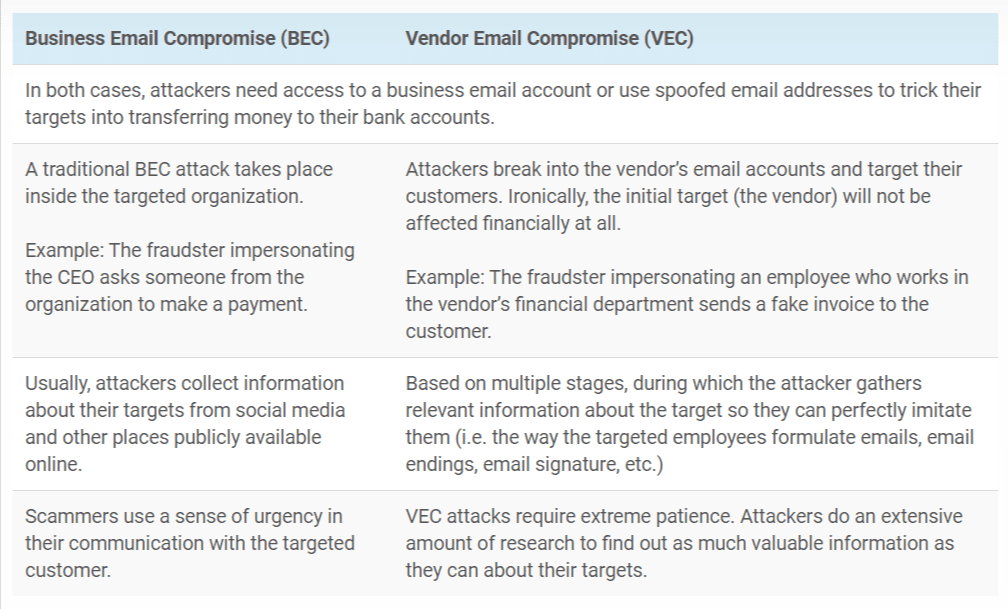
VEC attacks do not necessitate any more hacking skills than classic BEC attacks, but they do require the malicious actors to invest more time in the implementation.
But, as we all know, great patience pays off: successful VEC cyberattacks are able to cause significant damage to a company’s partners, clients, and other key stakeholders.
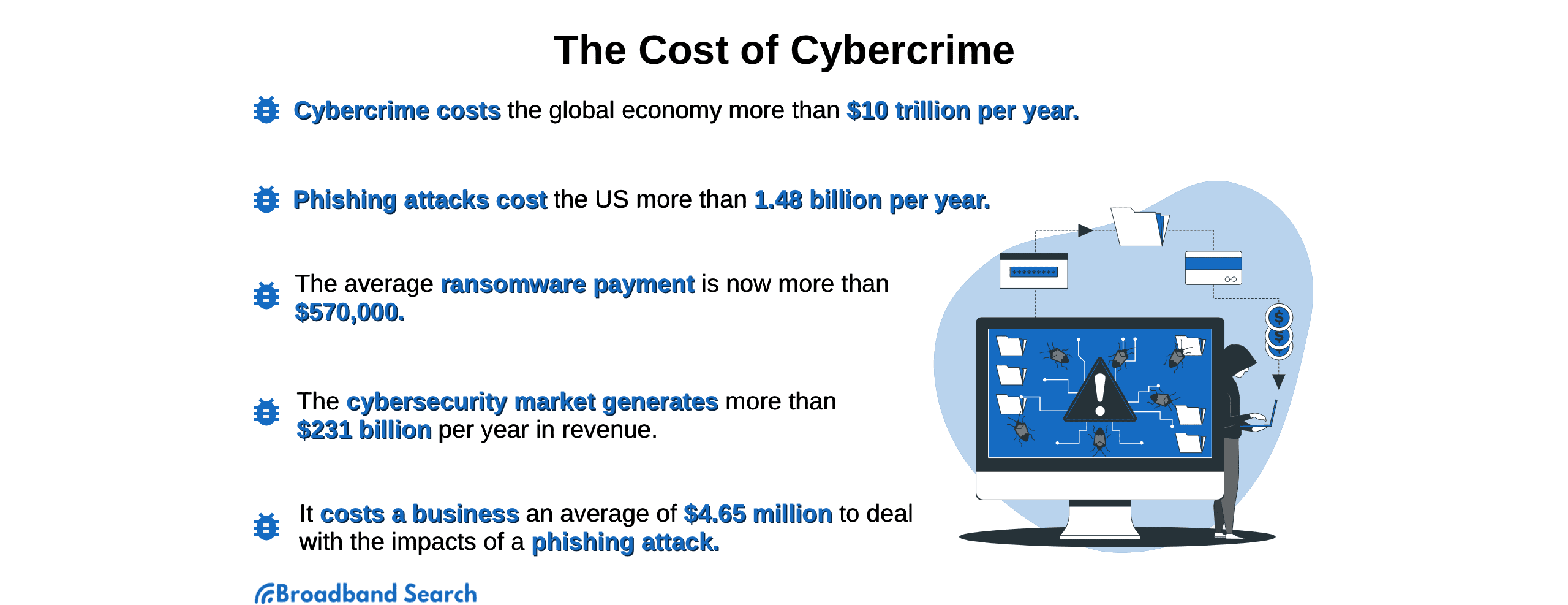
VEC attacks are a serious threat to businesses of all sizes. In 2022, the FBI reported that VEC attacks resulted in losses of over $2.7 billion. Over the past five years, losses from BEC attacks have more than doubled, growing by a staggering 111% between 2018 and 2022.
Common steps to every vendor email compromise attack:
-
- Conduct in-depth research on the vendor and their client base. Using publicly available information, attackers will learn about their target vendor’s employees, customers, work processes, billing cycles, and other facts. This process may take weeks or months to complete, but the research ultimately helps the attacker impersonate the defender more convincingly
- Sending phishing emails to the vendor. Before carrying out attacks against their final targets, attackers must first obtain access to the targeted vendor’s email account. To do this, attackers often send several phishing emails to the vendor that contain malicious links.
- Take over the compromised account. Once attackers gain access to the vendor’s email account, they create email forwarding rules to send relevant email copies to the attacker’s inbox. From here, the attacker will monitor the inbox for pertinent financial information such as bank account, invoice details, and payment schedules.
- Send targeted vendor email attacks to the vendor’s customers. The last step is to design a highly sophisticated and hard to detect spear phishing campaign email to the vendor’s customers, typically around the time of billing. Using the information gleaned from the research phase, attackers typically try to persuade their victims that they owe the vendor money, and to send the supposedly ‘required payment’ to the attacker’s account.
Key features of VEC attacks:
-
- They target businesses that have a relationship with a third-party vendor.
- They use social engineering techniques to trick the victim into believing that the email is legitimate.
- They often request payment for an overdue invoice or ask for sensitive information.
- They can be difficult to detect, as they may appear to be from a legitimate source.
Both VEC and BEC attacks are serious threats to businesses of all sizes.
Businesses can take steps to protect themselves from both types of attacks, such as implementing strong security controls for vendor access, educating employees about phishing attacks, and monitoring email traffic for suspicious activity.
In addition to these general security measures, businesses can also take specific steps to mitigate the risk of VEC attacks:
-
- Require vendors to use a secure email gateway. A secure email gateway can help to filter out malicious emails before they reach employees’ inboxes.
- Use a vendor risk management platform. A vendor risk management platform can help businesses to assess the security posture of their vendors and identify those that are most at risk of being compromised.
- Regularly monitor vendor security logs. By regularly monitoring vendor security logs, businesses can detect suspicious activity early on and take steps to mitigate the risk of a VEC attack.
- Implement strong security controls for vendor access. This includes requiring vendors to use strong passwords and two-factor authentication, and to regularly change their passwords.
- Educate employees about phishing attacks. Employees should be aware of the signs of a phishing email, and they should never click on links or open attachments in emails from unknown senders.
- Monitor email traffic for suspicious activity. Businesses should use a security solution that can detect and block phishing emails.
- Report suspicious emails to the IT department immediately. If an employee receives an email that they believe is suspicious, they should report it to the IT department immediately.
What to do if you receive a suspicious email:
-
- Call the person to verify that the request is legitimate.
- Double-check the email address of the sender to make sure it isn’t being spoofed.
- Avoid replying to the sender, especially if this is being received from a personal email address.
- Instead, forward your response to what you know is their actual work email address or call them by a phone number you know is legitimate.
- Be wary of changes in how the sender communicates, especially if you are asked to maintain secrecy or if the tone is urgent.
- Be especially suspicious if a supplier or vendor asks for their payment information to be changed.
- If you do fall victim to a BEC, it is very important to alert your manager quickly. If funds were transferred, there may be a chance to freeze the process and recover the funds.
Conclusion
If you are a vendor, you should train your employees to be extra cautious when establishing any kind of contact with both your customers and internal stakeholders.
If you are a company engaged in business relationships with vendors, the same rules apply.
Without a doubt, you can never be too careful, as you never know where malicious actors and advanced cyber threats may be hiding.
Need help?
Do you need help with email security, employee training, or more? Contact us to learn how PCA Technology Solutions can partner with you to help secure your business.


