by PCA Contributor | Feb 13, 2024 | Coaching, Managed Solutions
This video was filmed at @RealNewsCommunicationsNetwork broadcasting in North Dallas at the Lincoln Centre right next to the Galleria. ➤ https://www.realnewscn.com/contact More information: ➤ https://jeffcrilleyshow.com/ ➤ https://launchashow.com/ Blog Library The...

by PCA Contributor | Feb 8, 2024 | Event, Featured
A Journey of Heart In July 2020, amidst the challenges of the COVID-19 pandemic, PCA’s own Steve Bohn, experienced a life-altering event – a heart attack. Steve’s story began with a series of perplexing symptoms that sparked in him a surreal experience. Waves...

by PCA Contributor | Jan 9, 2024 | Event
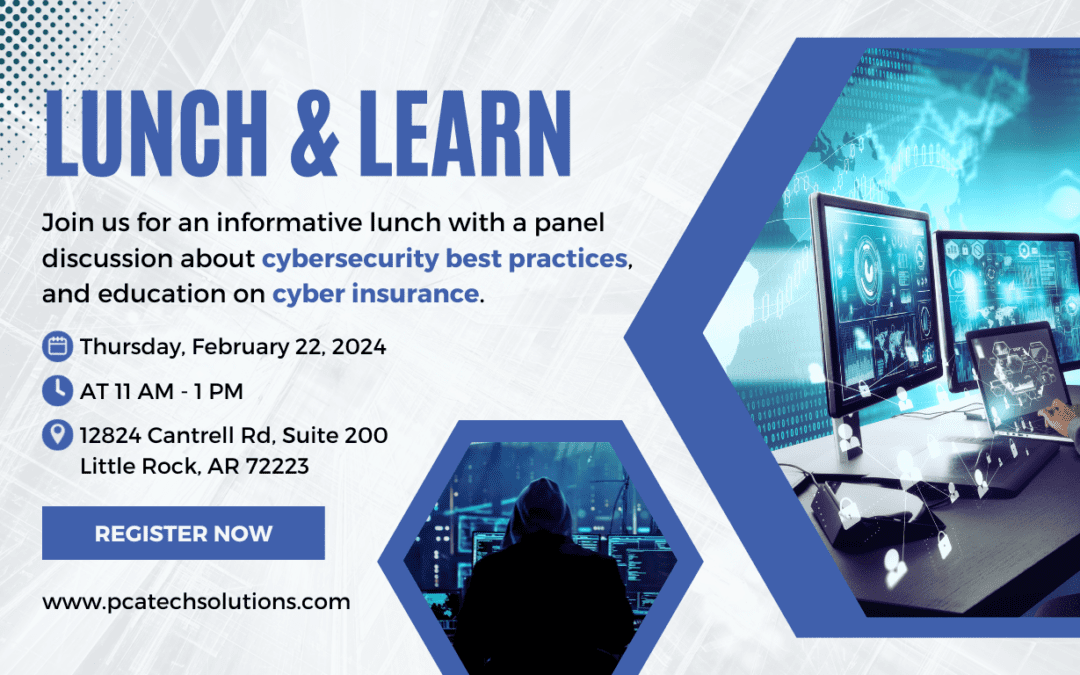
Details Cyber Insurance: Insurers have made it more difficult for companies to obtain and maintain cyber insurance policies, while at the same time eliminating coverage for some forms of breach. These challenges and frustrations might lead some organizations to pass...

by PCA Contributor | Jan 2, 2024 | Coaching, Managed Solutions
5 Benefits of Using a Technology Provider for Procurement Needs In today’s fast-paced business world, every company needs a reliable and efficient procurement process for its IT needs. Managing the procurement of IT hardware, software, and services can be...

by PCA Contributor | Dec 13, 2023 | Backup Management, Coaching, Managed Solutions
10 Most Common Small Business Technology Mistakes Small businesses are typically good at making the most out of everything possible to get by on less. However, this often causes several common mistakes when it comes to technology. These mistakes can lead to lost...